Understanding the different types of OTP and where an OTP generator fits in. The Messaging sector is seamlessly enlarging day to day, and we as a sector representatives are eager to share the information corresponding:
Providing secure access to applications and cloud-based software is a constant challenge for companies across all industries. Empowering users with simple but reliable security is critical to protecting user information and sensitive company data.
One of the ways technology companies have counteracted password theft and other types of cyberattacks is through the use of one-time passwords (OTPs). OTP is a form of multi-factor authentication (MFA) designed to make it much harder for hackers to access protected information.
MFAs require additional credentials beyond a simple password before the end user can gain access to an application or system. For example, an MFA that uses SMS will send the user a text with a numeric string that has to be entered before they are granted access. That code is a type of OTP.
Both B2B and B2C companies have an incentive to protect their user and company data while maintaining a great user experience (UX), which means that whatever security solution they choose, it needs to be streamlined without drastically interfering with a user’s workflow.
OTP authentication is an elegant solution to both security concerns and UX. There are two types of OTP: HOTP and TOTP. We’ll get into the differences of each below. But first, let’s dig a little deeper into OTP.
What is OTP and How Does it Work?
An OTP is like a password but it can only be used once, thus it stands for one-time password. It is often used in combination with a regular password as an additional authentication mechanism providing extra security.
OTPs are exactly what they sound like: one and done. Once you’ve used that password once, it’s dumped, and the next time you need to get into that application, you will use another one. Doing this increases security and makes it a lot harder for bad actors to penetrate private accounts.
Users can access an OTP for a given application or website through smartphone apps, a text message, or a proprietary token (such as a key fob). OneLogin Protect is an example of an OTP generator that you can use as an app on your phone. Any time you receive an SMS text with a code to help you get into a website or application, you’re using an OTP.
There are a variety of industry standard algorithms, such as SHA-1, that generate OTPs. All of these algorithms use two inputs to generate the OTP code: a seed and a moving factor. The seed is a static value (secret key) that’s created when you establish a new account on the authentication server.
While the seed doesn’t change, the moving factor does each time a new OTP is requested. How the moving factor is generated is the big differentiator between HOTP and TOTP.
What is HOTP?
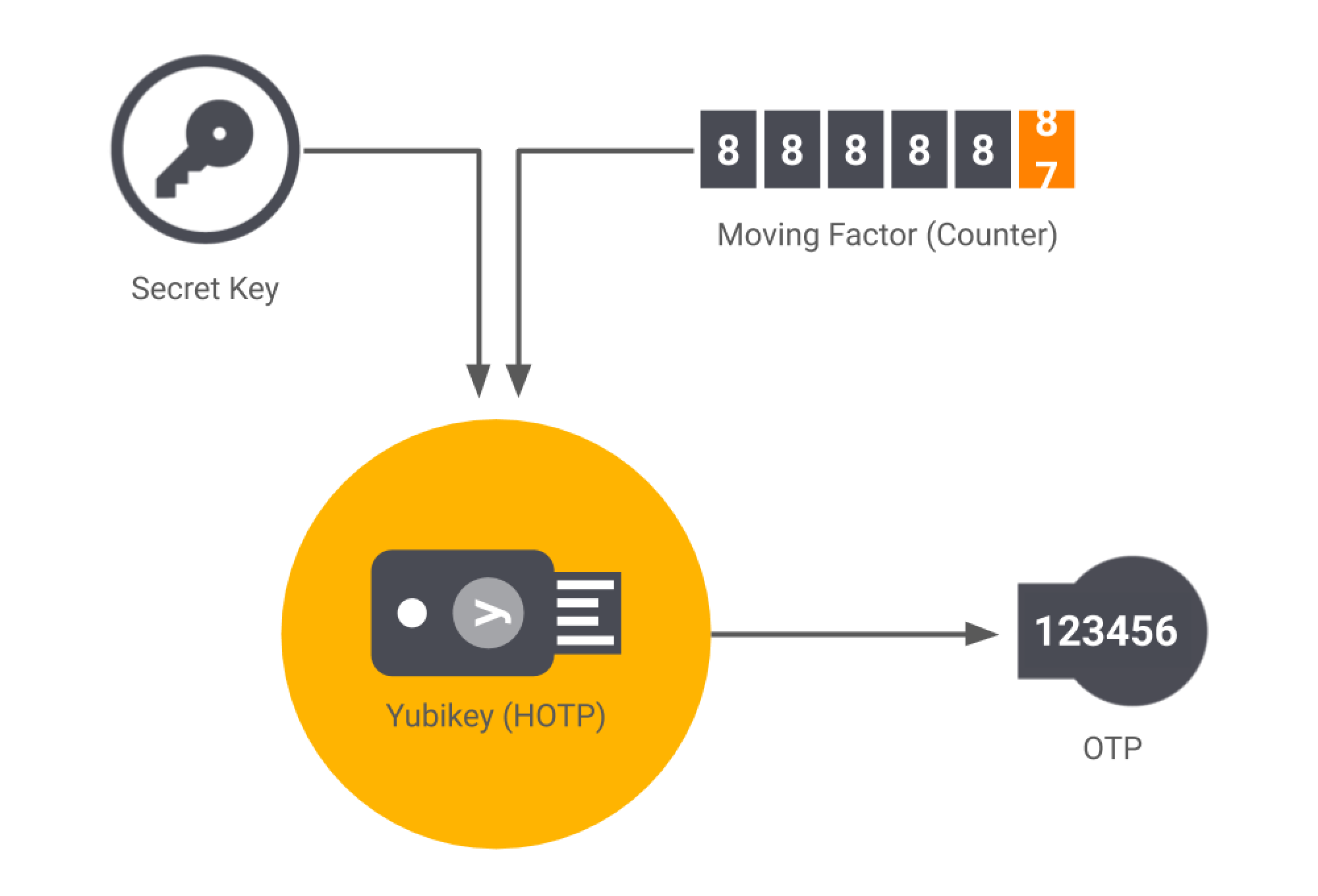
The “H” in HOTP stands for Hash-based Message Authentication Code (HMAC). Put in layman’s terms, HMAC-based One-time Password algorithm (HOTP) is an event-based OTP where the moving factor in each code is based on a counter.
Each time the HOTP is requested and validated, the moving factor is incremented based on a counter. The code that’s generated is valid until you actively request another one and it’s validated by the authentication server. The OTP generator and the server are synced each time the code is validated and the user gains access. Yubiko’s Yubikey is an example of an OTP generator that uses HOTP.
What is TOTP?
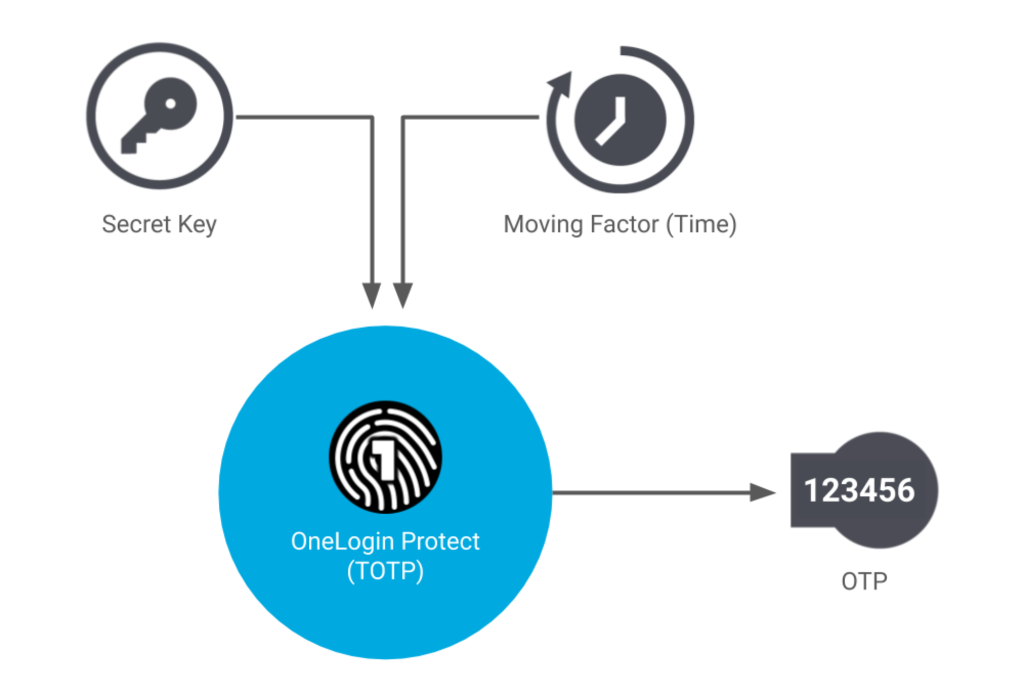
Time-based One-time Password (TOTP) is a time-based OTP. The seed for TOTP is static, just like in HOTP, but the moving factor in a TOTP is time-based rather than counter-based.
The amount of time in which each password is valid is called a timestep. As a rule, timesteps tend to be 30 seconds or 60 seconds in length. If you haven’t used your password within that window, it will no longer be valid, and you’ll need to request a new one to gain access to your application.
Limitations and Advantages
While both are far more secure than not using MFA at all, there are limitations and advantages to both HOTP and TOTP. TOTP (the newer of the two technologies) is easy to use and implement, but the time-based element does have a potential for time-drift (the lag between the password creation and use). If the user doesn’t enter the TOTP right away, there’s a chance it will expire before they do. So the server has to account for that and make it easy for the user to try again without automatically locking them out.
Since HOTP doesn’t have the time-based limitation, it’s a little more user-friendly, but may be more susceptible to brute force attack. That’s because of a potentially longer window in which the HOTP is valid. Some forms of HOTP have accounted for this vulnerability by adding a time-based component to their code, somewhat blurring the lines between these two types of OTP.
For non technology people abbreviation for SMS messaging sector in B2B.